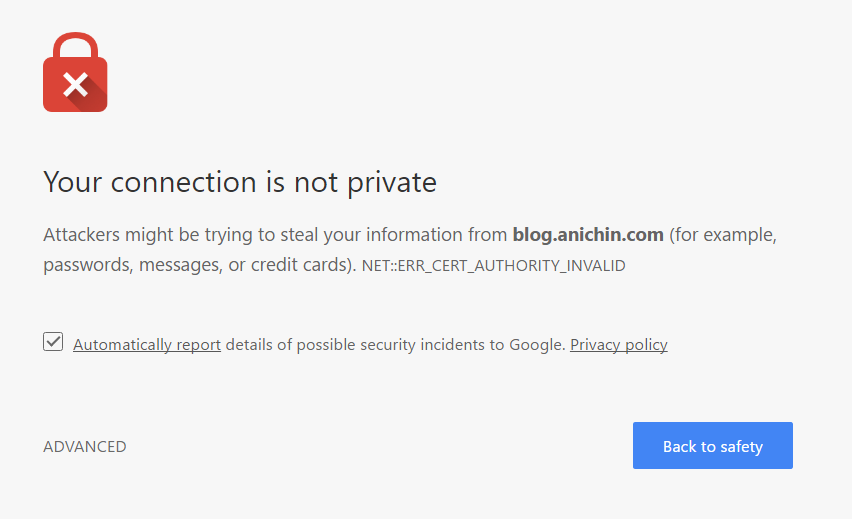
Problem
How to enable TLS 1.2 on Windows Server 2008 R2?
Resolution
QuoVadis recommends enabling and using the TLS 1.2 protocol on your server. TLS 1.2 has improvements over previous versions of the TLS and SSL protocol which will improve your level of security. By default, Windows Server 2008 R2 does not have this feature enabled. This KB article will describe the process to enable this.
- Start the registry editor by clicking on Start and Run. Type in “regedit” into the Run field (without quotations).
- Highlight Computer at the top of the registry tree. Backup the registry first by clicking on File and then on Export. Select a file location to save the registry file.
- Browse to the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols - Right click on the Protocols folder and select New and then Key from the drop-down menu. This will create new folder. Rename this folder to TLS 1.2.
- Right click on the TLS 1.2 key and add two new keys underneath it.
- Rename the two new keys as:
- Client
- Server
- Right click on the Client key and select New and then DWORD (32-bit) Value from the drop-down list.
- Rename the DWORD to DisabledByDefault.
- Right-click the name DisabledByDefault and select Modify… from the drop-down menu.
- Ensure that the Value data field is set to 0 and the Base is Hexadecimal. Click on OK.
- Create another DWORD for the Client key as you did in Step 7.
- Rename this second DWORD to Enabled.
- Right-click the name Enabled and select Modify… from the drop-down menu.
- Ensure that the Value data field is set to 1 and the Base is Hexadecimal. Click on OK.
- Repeat steps 7 to 14 for the Server key (by creating two DWORDs, DisabledByDefault and Enabled, and their values underneath the Server key).
- Reboot the server.
Your server should now support TLS 1.2.